How can businesses maintain data privacy across complex global networks? What strategies can be employed to ensure compliance with various information protection regulations? Companies must adopt robust security frameworks that protect data and ensure compliance. This article explores how companies can leverage secure network architectures like Secure Access Service Edge to maintain data privacy and meet global compliance standards.
Secure Access Service Edge and Security
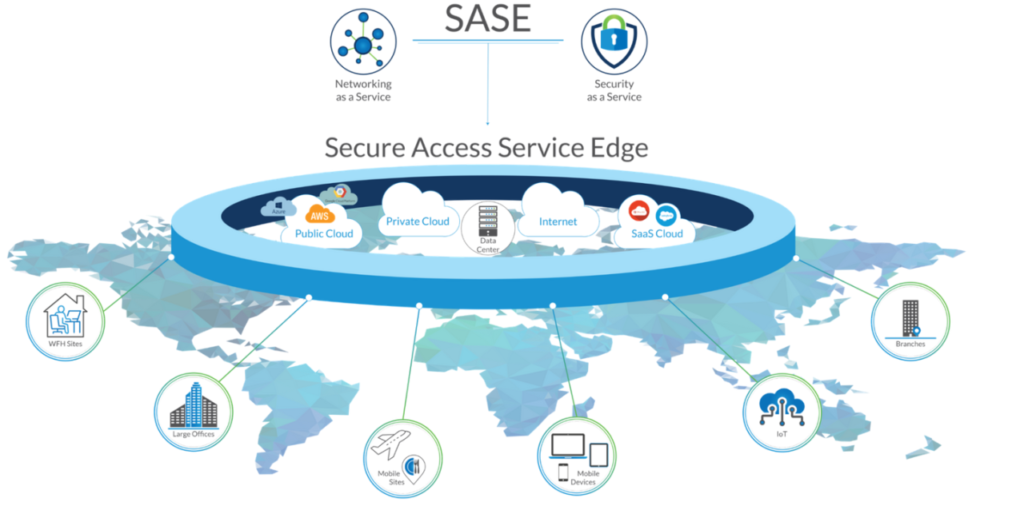
Secure Access Service Edge or SASE is a network architecture that converges wide-area networking and network security into a single, cloud-delivered service. This approach allows businesses to secure access to information and applications regardless of the user’s location. As such, businesses can create a more unified and efficient framework for managing privacy.
How Does It Enhance Data Privacy?
SASE does this by providing consistent security policies across all access points in the network. This consistency is crucial for ensuring that protection measures are uniformly applied, regardless of where the information is accessed or stored. Additionally, this network architecture supports encryption, identity verification, and access control.
Implementing Compliance Across Global Networks
Ensuring Compliance with Regional Regulations
To maintain compliance, businesses must first understand each region’s specific regulations. This includes understanding data residency requirements, consent regulations, and breach notification protocols. By aligning their security frameworks with these regional requirements, businesses can ensure that they remain compliant across all jurisdictions.
Centralizing Data Management and Security Policies
This is one effective strategy for ensuring global compliance. Centralization allows businesses to enforce consistent privacy practices across all regions. This approach reduces the complexity of managing multiple disparate security policies and ensures that all data is protected according to the highest standards.
Best Practices to Implement
Regular Audits and Assessments
These audits should evaluate the effectiveness of security measures to identify potential vulnerabilities. They should ensure that all data handling practices comply with relevant regulations. Regular assessments also allow for updating security policies in response to new threats or regulatory changes.
Employee Training and Awareness
Employees must know the importance of data privacy and understand how to handle sensitive information appropriately. Regular training sessions should cover identifying phishing attempts and securely managing information. They should also ensure that employees understand the company’s privacy policies.
Leveraging Advanced Security Technologies
Businesses should leverage advanced security technologies to enhance data privacy. This includes using encryption to protect data in transit and at rest, deploying multi-factor authentication to verify user identities. Implementing continuous monitoring helps detect and respond to threats in real-time. These technologies are integral to building a secure and compliant network infrastructure.
Pivotal Considerations
Balancing Security with Performance
One key challenge in implementing robust data privacy measures is balancing security with network performance. Strong security controls can impact the speed and efficiency of network operations. Businesses must carefully select solutions that provide the necessary security without compromising performance. It ensures that both data privacy and operational efficiency are maintained.
Adapting to Evolving Regulations
Businesses must be agile in adapting to security and regulatory changes. This requires staying informed about new regulatory developments and being prepared to update security practices as needed. Adopt flexible security frameworks that can be easily modified in response to regulatory changes. This is essential for long-term compliance.
Ensuring data privacy and compliance across global networks is a critical business task. By leveraging advanced network architectures like SASE, businesses can protect sensitive information and comply with diverse regulations. As data privacy regulations evolve, companies must remain vigilant and adaptable. They should ensure that their data privacy strategies are always aligned with the latest requirements.